Comprehensive Security for All Your Online Transactions
OTS-1100 protects your OS 2200 online transactions from unauthorized use by validating user credentials in relation to transaction functions. You can establish a secure transaction environment without changing your online programs.
You can also use OTS in conjunction with DPS to implement field-level security.
If you are able to modify your application programs, you can use the application interface (AI) in OTS to deliver authorization data to the executing program. That program can then make detailed decisions to permit or withhold individual transaction functions, based on the user’s security profile.
OTS-1100 provides flexible options for its installation and configuration. You choose the method most compatible with your site standards and existing online infrastructure.
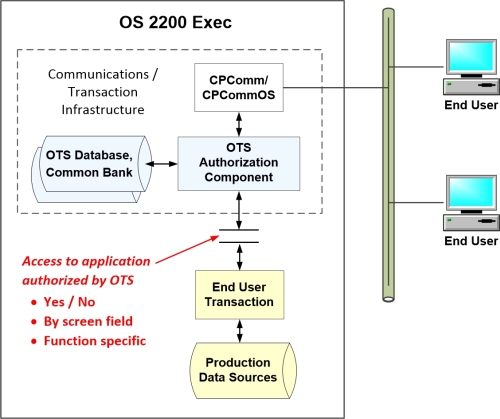
OTS-1100 interoperates with Unisys’ offerings within their communications and transaction ecosystem:
Key Features
Release Announcements
Product Description
For all your online applications
You choose how to install OTS depending on the transaction deployment philosophy at your site.
Your systems administrators install an OTS-1100 modules in one or more components of your transaction infrastructure. The OTS module authorizes users based on their security profile and the requirements of the transaction they wish to access.
Each implementation option is briefly summarized below. For some sites, the best solution is a combination of methods.
For more information, click on the button “Product Description.”
MCB Implementation
You BUILD MCB with an OTS-1100 module included. When the user executes a transaction, MCB checks first with OTS to see if the user is authorized. If not, the user’s request is rejected. This method is highly efficient because an unauthorized attempt doesn’t even load the transaction.
TIP Implementation
You BUILD TIP with an OTS modification to the module INITAL. When the user executes a transaction, the transaction’s call to CINIT in the INITAL module first checks with OTS to see if that user is authorized. If not, the user’s request is rejected.
DPS Implementation
You BUILD DPS with an OTS modification to the modules ACOB/INTERFACE or UCS/INTERFACE. You can implement two kinds of protection.
OTS Application Interface (AI)
Programmers compile and link their transaction program with the OTS-1100 Application Interface (AI) module. When the user executes the program, it immediately calls OTS and obtains the user’s OTS security profile. The transaction can then make fine-grained decisions about which functions to authorize, based on the user’s profile.
Protect and manage your online applications.
Flexible implementation. Easy to use. Strengthens your enterprise security.
